The AD Hacking series is going to bring lots of content about hacking into Active Directory environments. The goal here is to present the theory of how these contexts work behind the curtains, the way it opens space for maaany vulnerabilities and misconfigurations inside a corporate network, and specially multiple ways you can leverage and exploit that as an Ethical Hacker.
Lab Demonstrations
Most articles in the series will present the main tools we can use to exploit flaws with placeholders for you to replace according to the context of your test, HOWEVER, there will always be example DEMOs in there too, so you can see the usage in a simulated lab environment!
So pay attention to the places where you find “Demo on GOAD Lab” written in green, if you click that you’ll open up the demonstration parts of the article, which will contain both screenshots and command snippets for you to copy! Example down below:
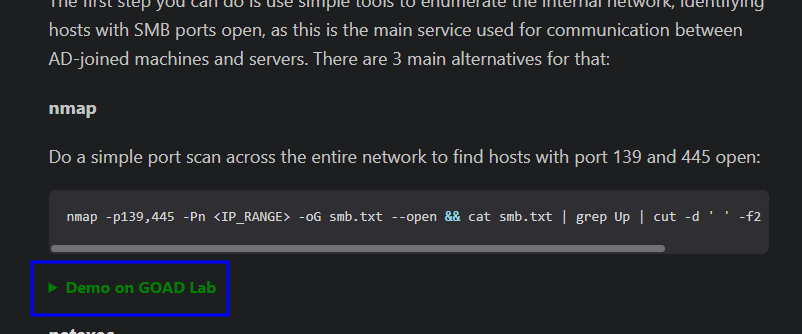
When you click in the dropdown, the content is shown:
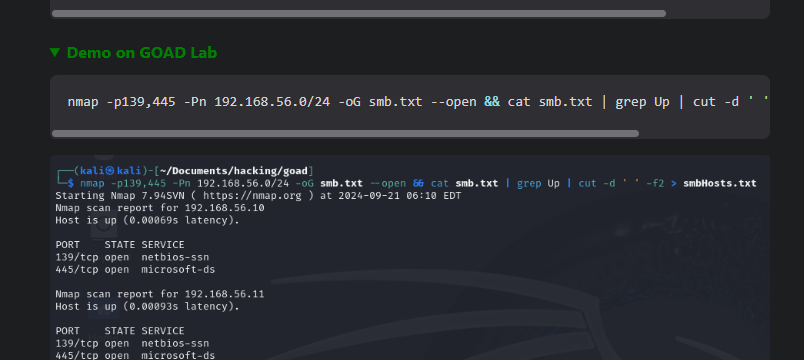
Lab Environment
Most of the attack demonstrations will be done in the Game of Active Directory (GOAD) lab environment. If you want to, you can setup the lab in your own machine with Virtualbox or VMware, or even use the Azure setup the tool also made available recently:
This lab has 5 machines, spread across 2 forests with a total of 3 domains. You’ll see in the demos that the usernames are from Game of Thrones too. Just so you can locate yourself in the structure of the lab when following the demos, here is the general schema:
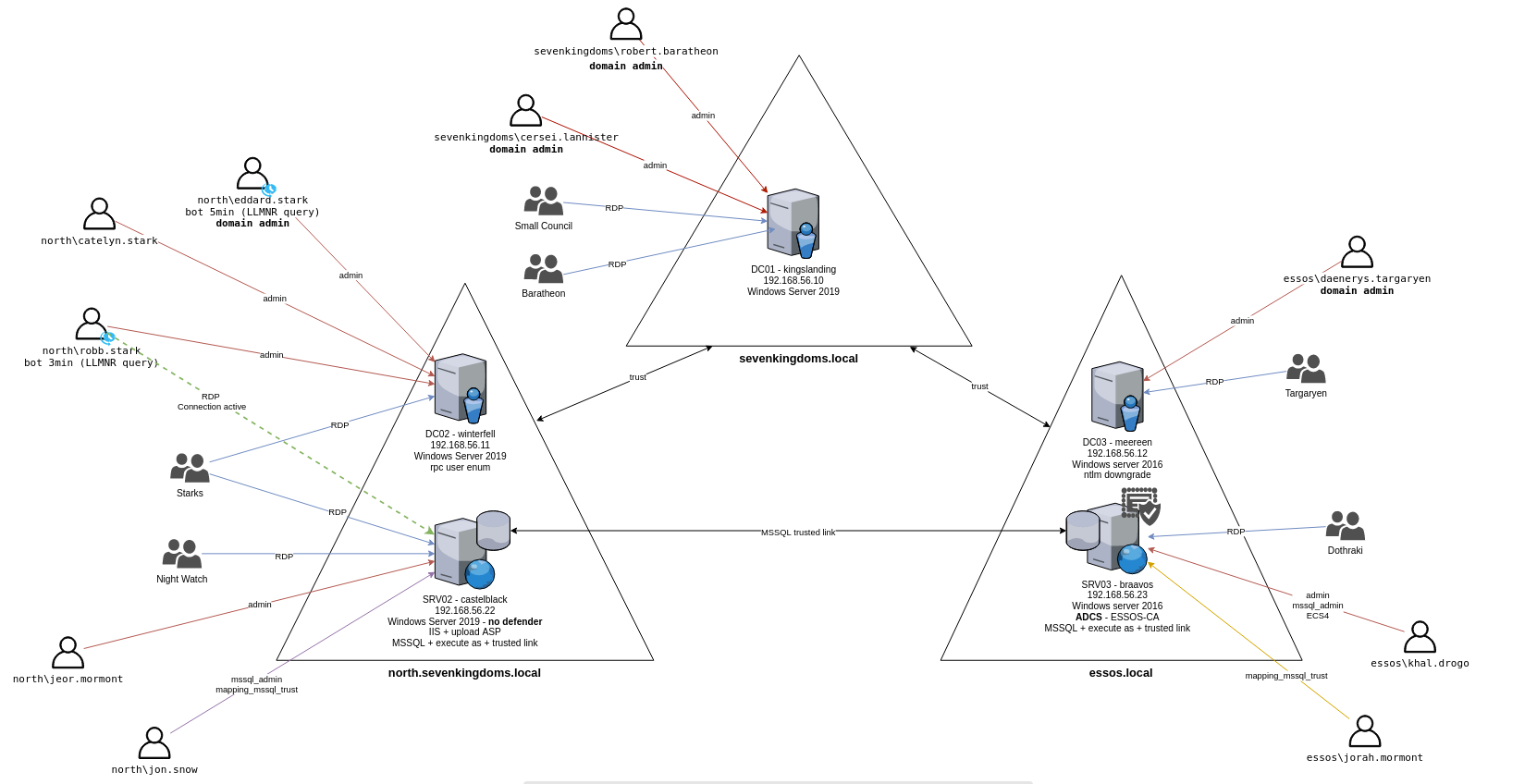
The lab creators also have a really good writeup in the link below. Although it does not explain much of the theory of how things work, it does a great job guiding you through the attacks!
List of Articles
In order to list all available contents in this series, just click on the [AD Hacking] tag at the end of one of the articles, or follow this link: